✅ Prerequisites
Before you begin, you’ll need:-
Snowflake Account Identifier
You can find this in your account settings:
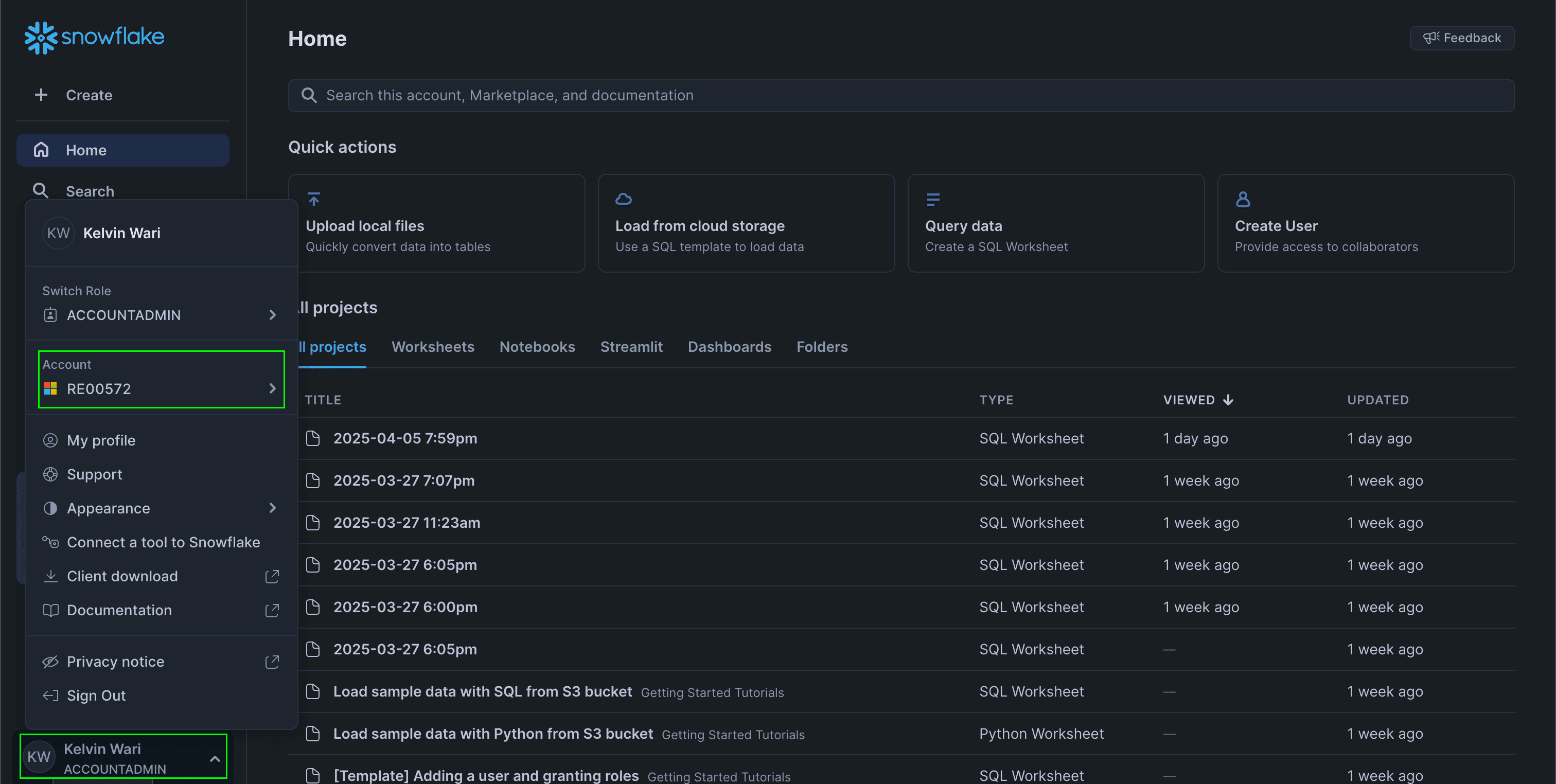
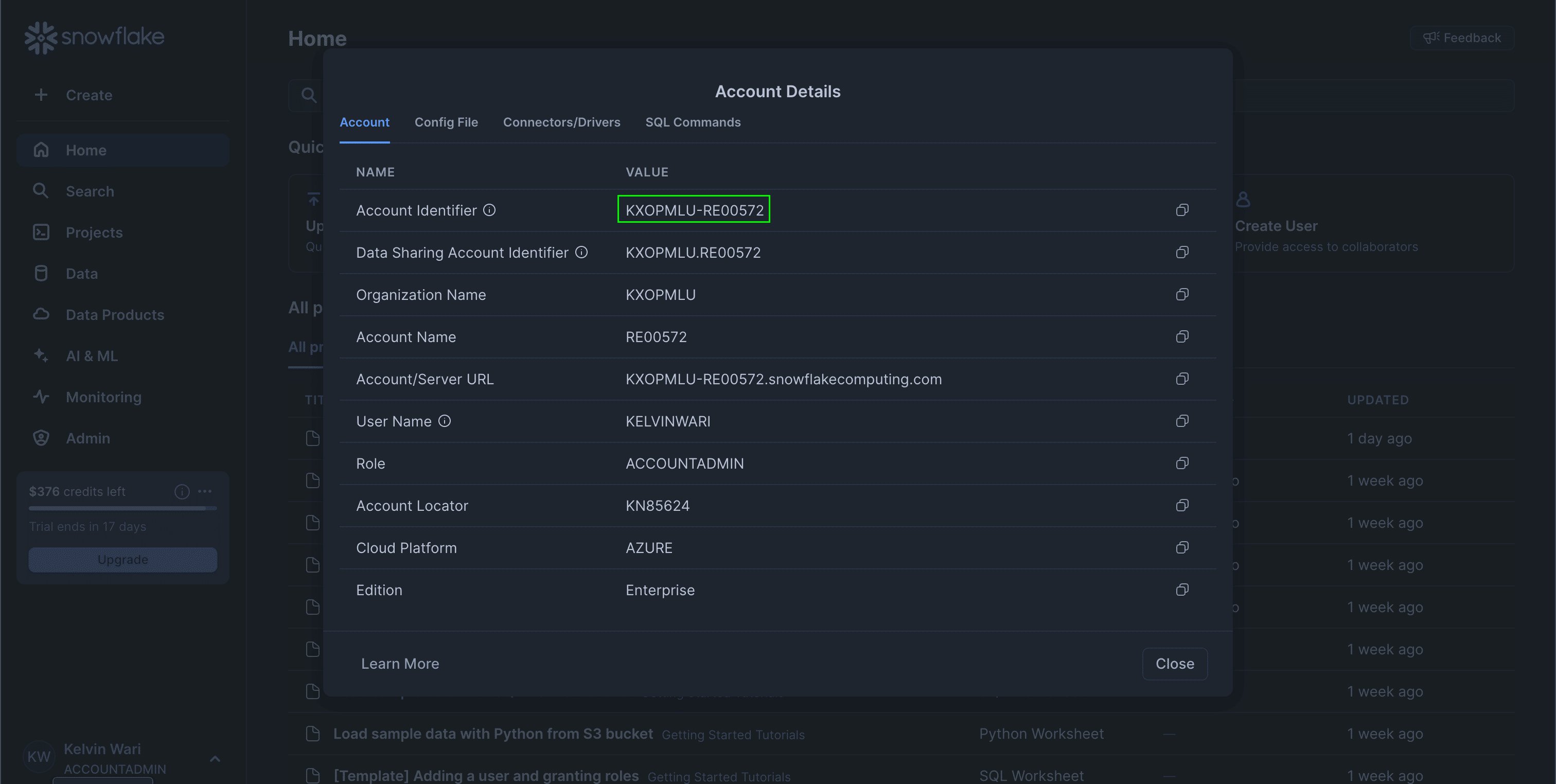
-
Snowflake Username
You can use your existing user or create a dedicated service user for Hunch.
Optional: Create a Dedicated Service User
If you prefer to use a dedicated service user, run this SQL in your Snowflake UI:
🛡️ Step 1: Set Up Role and Permissions
First, we need to set up the necessary permissions for Hunch to access your data. Run the following SQL in your Snowflake UI:<database>: Your database name<schema>: Your schema name<warehouse>: Your warehouse name<your_username_or_service_user>: Your username or service user name
🔐 Step 2: Generate a Authentication Keys
To establish a secure connection, you’ll need to generate a key pair. Open your terminal and run:- This will generate two files:
private_key.pem→ Keep this secure! You’ll need to upload this to Hunch.public_key.pem→ Copy the entire output as a single line.
🔁 Step 3: Attach the Public Key to the Snowflake User
Attach the public key to your Snowflake user by running this SQL command:<your-public-key> with your public key
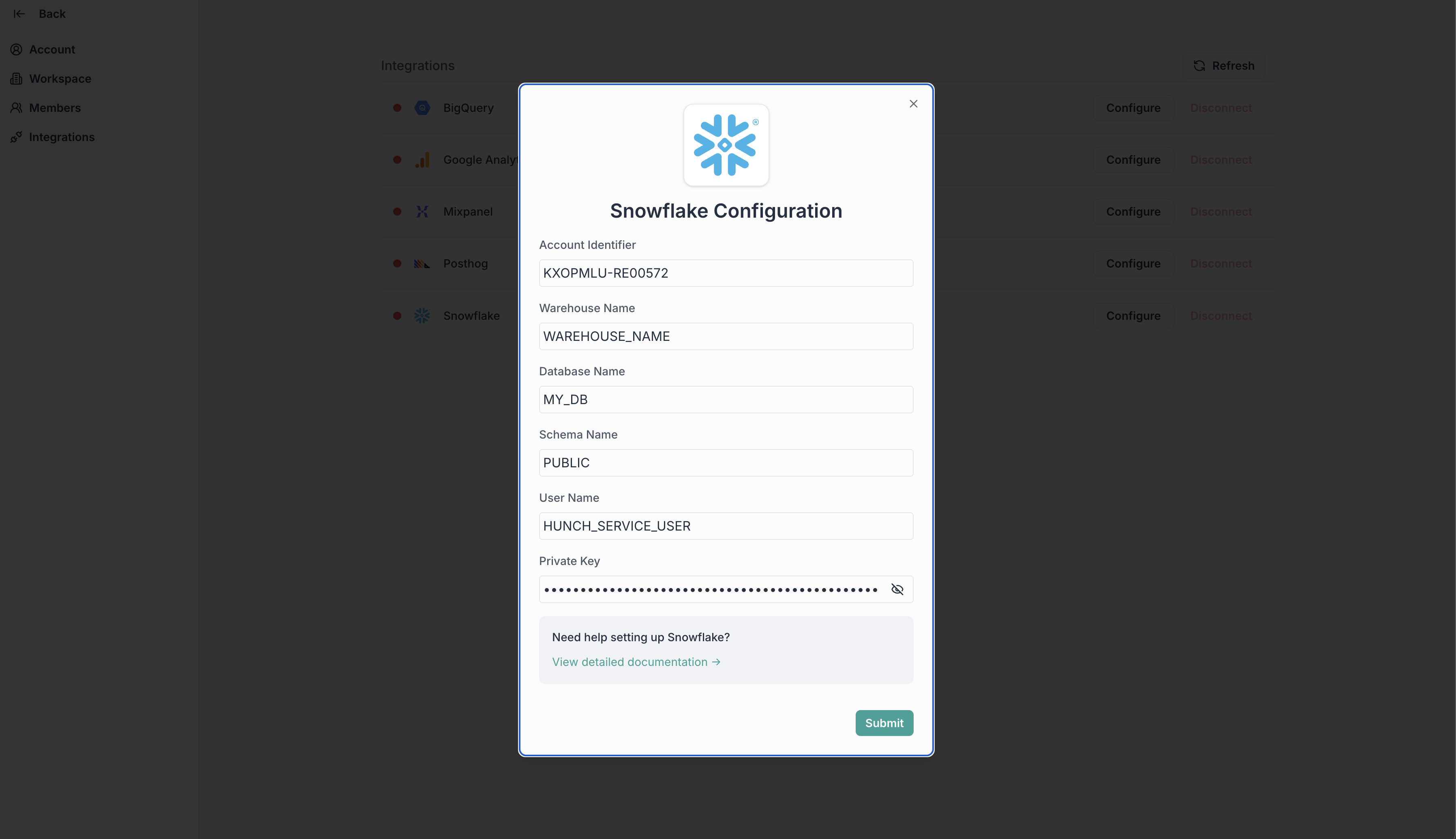
🧩 Step 5: Fill the Hunch Integration Form
- Log into Hunch.dev
- Click on your organization name > Connect Data
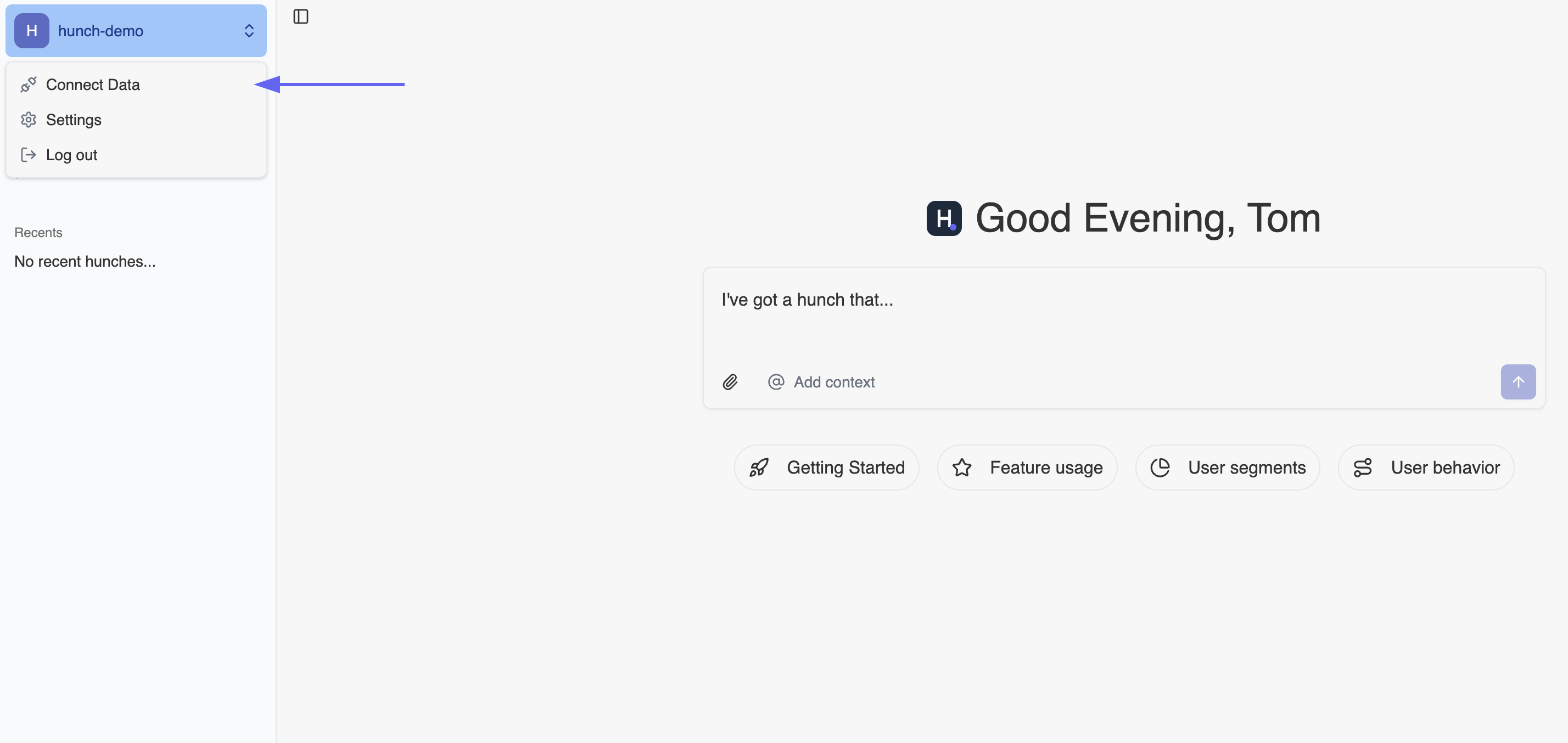
- Click Configure on the Snowflake row
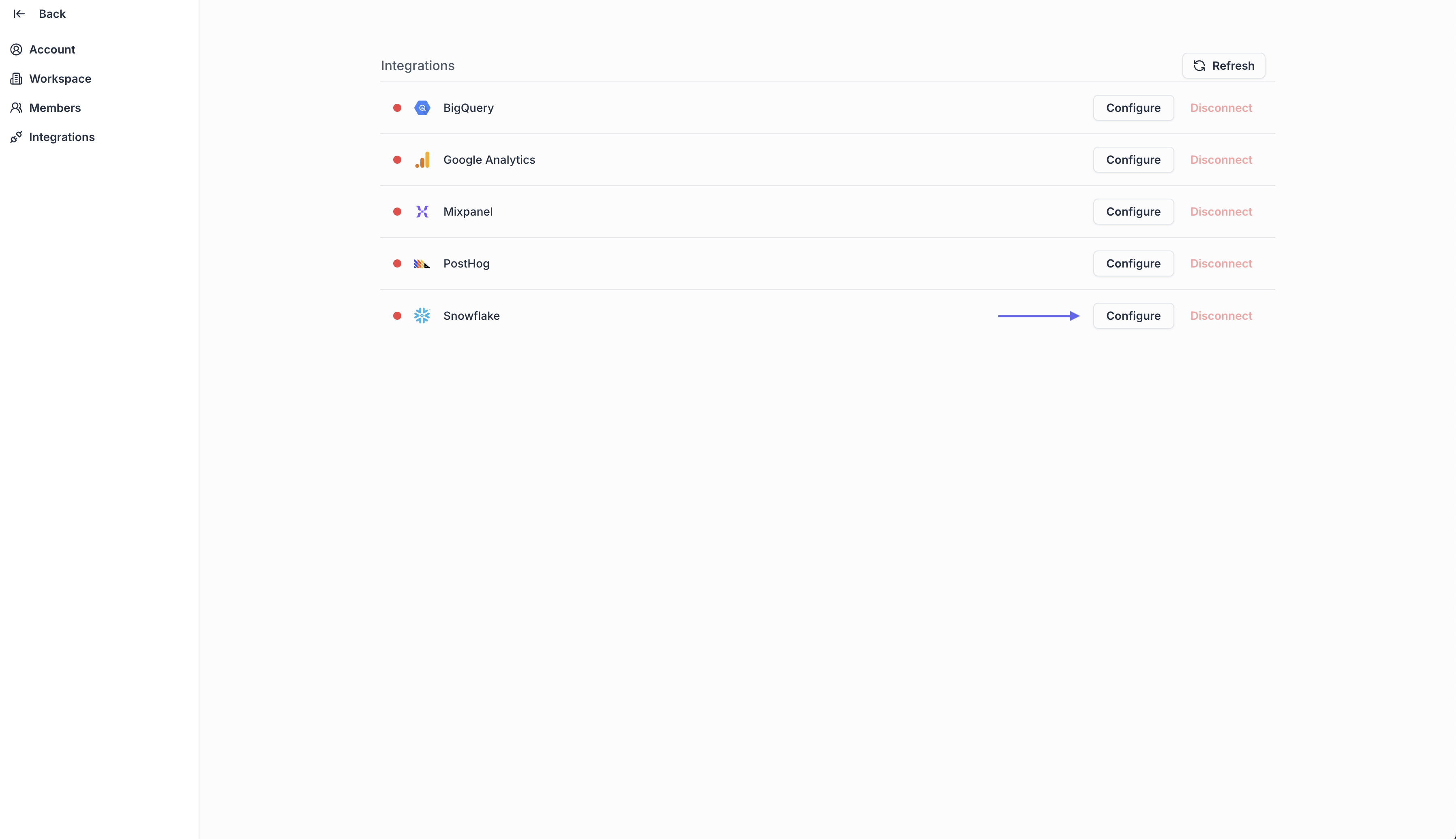
-
Description
A name for this connection (e.g., “My Snowflake”). -
Account Identifier
Your Snowflake account identifier (e.g.,KXOPMLU-RE00572). -
Warehouse Name
The name of your Snowflake warehouse (e.g.,WAREHOUSE_NAME). -
Database Name
The name of your Snowflake database (e.g.,MY_DB). -
Schema Name
The schema you want to use (e.g.,PUBLIC). -
User Name
The username or service user you created (e.g.,HUNCH_SERVICE_USER). -
Private Key
Paste the contents of yourprivate_key.pemfile (from Step 2). -
Click Submit
🎉 Done! You’re now connected
Need help? Ping us at support@hunch.dev🔒 A note on security
Note: Hunch uses JWT (JSON Web Token) authentication with RSA key pair, following Snowflake’s recommended security practices for third-party integrations. This method ensures no passwords are stored and provides strong cryptographic security for the connection.